[2021.5] Get the latest Oracle 1z0-1084-20 exam practice questions and free Pdf dumps from Leads4Pass
Share Oracle 1z0-1084-20 exam practice questions and answers from leads4pass latest updated 1z0-1084-20 dumps free of charge. Get the latest uploaded 1z0-1084-20 dumps pdf from google driver online. To get the full Oracle 1z0-1084-20 dumps PDF or dumps VCE visit: https://www.leads4pass.com/1z0-1084-20.html (Q&As: 72). all Oracle 1z0-1084-20 exam questions have been updated, the answer has been corrected!
Make sure your exam questions are real and effective to help you pass your first exam!
Table Of Content:
- Oracle 1z0-1084-20 Dumps Pdf
- Oracle 1z0-1084-20 Dumps Youtube
- Oracle 1z0-1084-20 Exam Practice Test
- Oracle Discount Code 2021
[Oracle 1z0-1084-20 Dumps pdf] Latest Oracle 1z0-1084-20 Dumps PDF collected by leads4pass Google Drive:
https://drive.google.com/file/d/1UuRcSyNEGxBxPK9IMlErLQ4tkPCvxWIt/
[Oracle 1z0-1084-20 Youtube] Oracle 1z0-1084-20 exam questions and answers are shared free of charge from Youtube watching uploads from leads4pass.
Latest Update Oracle 1z0-1084-20 Exam Practice Questions and Answers Online Test
QUESTION 1
Which statement accurately describes Oracle Cloud Infrastructure (OCI) Load Balancer integration with OCI Container
Engine for Kubernetes (OKE)?
A. OKE service provisions an OCI Load Balancer instance for each Kubernetes service with LoadBalancer type in the
YAML configuration.
B. OCI Load Balancer instance provisioning is triggered by OCI Events service for each Kubernetes service with
LoadBalancer type in the YAML configuration.
C. OCI Load Balancer instance must be manually provisioned for each Kubernetes service that requires traffic
balancing.
D. OKE service provisions a single OCI Load Balancer instance shared with all the Kubernetes services with
LoadBalancer type in the YAML configuration.
Correct Answer: D
If you are running your Kubernetes cluster on Oracle Container Engine for Kubernetes (commonly known as OKE), you
can have OCI automatically provision load balancers for you by creating a Service of type LoadBalancer instead of (or in
addition to) installing an ingress controller like Traefik or Voyage YAML file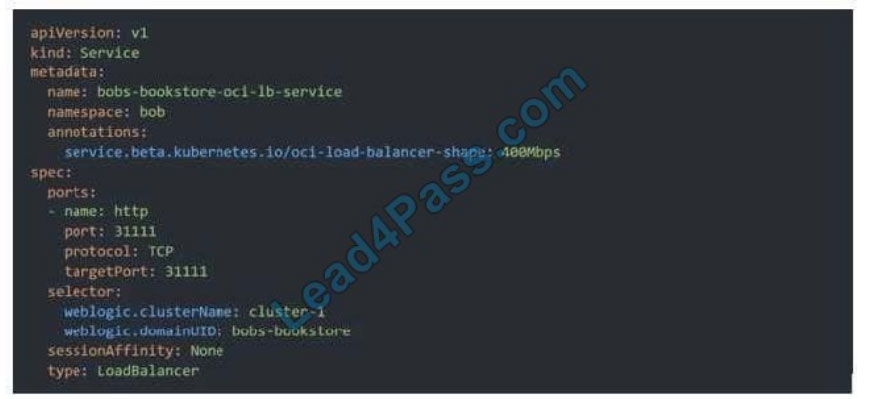
When you apply this YAML file to your cluster, you will see the new service is created. After a short time (typically less
than a minute) the OCI Load Balancer will be provisioned.
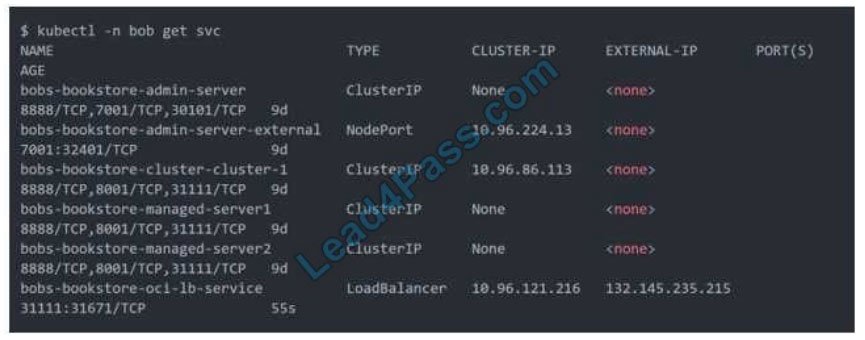
https://oracle.github.io/weblogic-kubernetes-operator/faq/oci-lb/
QUESTION 2
Which two statements accurately describe Oracle SQL Developer Web on Oracle Cloud Infrastructure (OCI)
Autonomous Database?
A. It is available for databases with dedicated Exadata infrastructure only.
B. After provisioning into an OCI compute Instance, it can automatically connect to the OCI Autonomous Databases
instances.
C. It is available for databases with both dedicated and shared Exadata infrastructure.
D. It provides a development environment and a data modeler interface for OCI Autonomous Databases.
E. It must be enabled via OCI Identity and Access Management policy to get access to the Autonomous Databases
instances.
Correct Answer: AD
Oracle SQL Developer Web in Autonomous Data Warehouse provides a development environment and a data modeler
interface for Autonomous Databases. SQL Developer Web is available for databases with both dedicated Exadata
infrastructure and shared Exadata infrastructure.
https://docs.cloud.oracle.com/enus/iaas/Content/Database/Tasks/adbtools.htm
QUESTION 3
A programmer Is developing a Node is application which will run in a Linux server on their on-premises
data center. This application will access various Oracle Cloud Infrastructure (OC1) services using OCI
SDKs.
What is the secure way to access OCI services with OCI Identity and Access Management (JAM)?
A. Create a new OCI IAM user associated with a dynamic group and a policy that grants the desired permissions to OCI
services. Add the on-premises Linux server in the dynamic group.
B. Create an OCI IAM policy with the appropriate permissions to access the required OCI services and assign the policy
to the on-premises Linux server.
C. Create a new OCI IAM user, add the user to a group associated with a policy that grants the desired permissions to
OCI services. In the on-premises Linux server, generate the keypair used for signing API requests and upload the public
key to the IAM user.
D. Create a new OCI IAM user, add the user to a group associated with a policy that grants the desired permissions to
OCI services. In the on-premises Linux server, add the user name and password to a file used by Node.js
authentication.
Correct Answer: C
Before using Oracle Functions, you have to set up an Oracle Cloud Infrastructure API signing key. The instructions in
this topic assume:
-you are using Linux
– you are following Oracle\\’s recommendation to provide a passphrase to encrypt the private key For more Detials Set
up an Oracle Cloud Infrastructure API Signing Key for Use with Oracle Functions
https://docs.cloud.oracle.com/en-us/iaas/Content/Functions/Tasks/functionssetupapikey.htm
QUESTION 4
A service you are deploying to Oracle infrastructure (OCI) Container En9ine for Kubernetes (OKE) uses a docker image
from a private repository Which configuration is necessary to provide access to this repository from OKE?
A. Add a generic secret on the cluster containing your identity credentials. Then specify a registrycredentials property in
the deployment manifest.
B. Create a docker-registry secret for OCIR with API key credentials on the cluster, and specify the imagepullsecret
property in the application deployment manifest.
C. Create a docker-registry secret for OCIR with identity Auth Token on the cluster, and specify the image pull secret
property in the application deployment manifest.
D. Create a dynamic group for nodes in the cluster, and a policy that allows the dynamic group to read repositories in
the same compartment.
Correct Answer: C
Pulling Images from Registry during Deployment During the deployment of an application to a Kubernetes cluster,
you\\’ll typically want one or more images to be pulled from a Docker registry. In the application\\’s manifest file you
specify the images to pull, the registry to pull them from, and the credentials to use when pulling the images. The
manifest file is commonly also referred to as a pod spec, or as a deployment.yaml file (although other filenames are
allowed). If you want the application to pull images that reside in Oracle Cloud Infrastructure Registry, you have to
perform two steps:
–
You have to use kubectl to create a Docker registry secret. The secret contains the Oracle Cloud Infrastructure
credentials to use when pulling the image. When creating secrets, Oracle strongly
recommends you use the latest version of kubectl To create a Docker registry secret: 1- If you haven\\’t already done
so, follow the steps to set up the cluster\\’s kubeconfig configuration file and (if necessary) set the KUBECONFIG
environment variable to point to the file. Note that you must set up your own kubeconfig file. You cannot access a
cluster using a kubeconfig file that a different user set up. 2- In a terminal window, enter: $ kubectl create secret dockerregistry –docker-server=.ocir.io –dockerusername=\\’/\\’ –docker-password=\\’\\’ –dockeremail=\\’\\’ where: is a name of
your choice, that you will use in the manifest file to refer to the secret . For example, ocirsecret is the key for the Oracle
Cloud Infrastructure Registry region you\\’re using. For example, iad. See Availability by Region. ocir.io is the Oracle
Cloud Infrastructure Registry name. is the auto-generated Object Storage namespace string of the tenancy containing
the repository from which the application is to pull the image (as shown on the Tenancy Information page). For example,
the namespace of the acme-dev tenancy might be ansh81vru1zp. Note that for some older tenancies, the namespace
string might be the same as the tenancy name in all lower-case letters (for example, acmedev). is the username to use
when pulling the image. The username must have access to the tenancy specified by . For example, [email protected] .
If your tenancy is federated with Oracle Identity Cloud Service, use the format oracleidentitycloudservice/ is the auth
token of the user specified by . For example, k]j64r{1sJSSF-;)K8 is an email address. An email address is required, but
it doesn\\’t matter what you specify. For example, [email protected]
–
You have to specify the image to pull from Oracle Cloud Infrastructure Registry, including the repository location and
the Docker registry secret to use, in the application\\’s manifest file.
QUESTION 5
You are developing a serverless application with Oracle Functions. Your function needs to store state in a database.
Your corporate security Standards mandate encryption of secret information like database
passwords.
As a function developer, which approach should you follow to satisfy this security requirement?
A. Use the Oracle Cloud Infrastructure Console and enter the password in the function configuration section in the
provided input field.
B. Use Oracle Cloud Infrastructure Key Management to auto-encrypt the password. It will inject the auto-decrypted
password inside your function container.
C. Encrypt the password using Oracle Cloud Infrastructure Key Management. Decrypt this password in your function
code with the generated key.
D. All function configuration variables are automatically encrypted by Oracle Functions.
Correct Answer: A
Passing Custom Configuration Parameters to Functions he code in functions you deploy to Oracle Functions will
typically require values for different parameters. Some pre-defined parameters are available to your functions as
environment variables. But you\\’ll often want your functions to use parameters that you\\’ve defined yourself. For
example, you might create a function that reads from and writes to a database. The function will require a database
connect string, comprising a username, password, and hostname. You\\’ll probably want to define username, password,
and hostname as parameters that are passed to the function when it\\’s invoked. Using the Console To specify custom
configuration parameters to pass to functions using the Console: Log in to the Console as a functions developer. In the
Console, open the navigation menu. Under Solutions and Platform, go to Developer Services and click Functions.
Select the region you are using with Oracle Functions. Oracle recommends that you use the same region as the Docker
registry that\\’s specified in the Fn Project CLI context (see 6. Create an Fn Project CLI Context to Connect to Oracle
Cloud Infrastructure). Select the compartment specified in the Fn Project CLI context (see 6. Create an Fn Project CLI
Context to Connect to Oracle Cloud Infrastructure). The Applications page shows the applications defined in the
compartment. Click the name of the application containing functions to which you want to pass custom configuration
parameters: To pass one or more custom configuration parameters to every function in the application, click
Configuration to see the Configuration section for the application. To pass one or more custom configuration parameters
to a particular function, click the function\\’s name to see the Configuration section for the function. In the Configuration
section, specify details for the first custom configuration parameter: Key: The name of the custom configuration
parameter. The name must only contain alphanumeric characters and underscores, and must not start with a number.
For example, username Value: A value for the custom configuration parameter. The value must only contain printable
unicode characters. For example, jdoe Click the plus button to save the new custom configuration parameter. Oracle
Functions combines the key-value pairs for all the custom configuration parameters (both application-wide and functionspecific) in the application into a single, serially-encoded configuration object with a maximum allowable size of 4Kb.
You cannot save the new custom configuration parameter if the size of the serially-encoded configuration object would
be greater than 4Kb. (Optional) Enter additional custom configuration parameters as required.
QUESTION 6
Which is NOT a valid option to execute a function deployed on Oracle Functions?
A. Send a signed HTTP requests to the function\\’s invoke endpoint
B. Invoke from Oracle Cloud Infrastructure CLI
C. Invoke from Docker CLI
D. Trigger by an event in Oracle Cloud Infrastructure Events service
E. Invoke from Fn Project CLI
Correct Answer: C
You can invoke a function that you\\’ve deployed to Oracle Functions in different ways:
Using the Fn Project CLI.
Using the Oracle Cloud Infrastructure CLI.
Using the Oracle Cloud Infrastructure SDKs.
Making a signed HTTP request to the function\\’s invoke endpoint. Every function has an invoke endpoint.
Each of the above invokes the function via requests to the API. Any request to the API must be
authenticated by including a signature and the OCID of the compartment to which the function belongs in
the request header. Such a request is referred to as a \\’signed\\’ request. The signature includes Oracle
Cloud Infrastructure credentials in an encrypted form.
QUESTION 7
You need to execute a script on a remote instance through Oracle Cloud Infrastructure Resource Manager. Which
option can you use?
A. Use /bin/sh with the full path to the location of the script to execute the script.
B. It cannot be done.
C. Download the script to a local desktop and execute the script.
D. Use remote-exec
Correct Answer: D
Resource Manager is an Oracle Cloud Infrastructure service that allows you to automate the process of provisioning
your Oracle Cloud Infrastructure resources. Using Terraform, Resource Manager helps you install, configure, and
manage resources through the “infrastructure-as-code” model. With Resource Manager, you can use Terraform\\’s
remote exec functionality to execute scripts or commands on a remote computer. You can also use this technique for
other provisioners that require access to the remote resource.
QUESTION 8
You have been asked to create a stateful application deployed in Oracle Cloud Infrastructure (OCI)
Container Engine for Kubernetes (OKE) that requires all of your worker nodes to mount and write data to
persistent volumes.
Which two OCI storage services should you use?
A. Use OCI File Services as persistent volume.
B. Use GlusterFS as persistent volume.
C. Use OCI Block Volume backed persistent volume.
D. Use open source storage solutions on top of OCI.
E. Use OCI Object Storage as persistent volume.
Correct Answer: AC
A PersistentVolume (PV) is a piece of storage in the cluster that has been provisioned by an administrator. PVs are
volume plugins like Volumes, but have a lifecycle independent of any individual Pod that uses the PV. A
PersistentVolumeClaim (PVC) is a request for storage by a user. It is similar to a Pod. Pods consume node resources
and PVCs consume PV resources. If you intend to create Kubernetes persistent volumes, sufficient block volume quota
must be available in each availability domain to meet the persistent volume claim. Persistent volume claims must
request a minimum of 50 gigabytes You can define and apply a persistent volume claim to your cluster, which in turn
creates a persistent volume that\\’s bound to the claim. A claim is a block storage volume in the underlying IaaS provider
that\\’s durable and offers persistent storage, enabling your data to remain intact, regardless of whether the containers
that the storage is connected to are terminated. With Oracle Cloud Infrastructure as the underlying IaaS provider, you
can provision persistent volume claims by attaching volumes from the Block Storage service.
QUESTION 9
You are developing a serverless application with Oracle Functions and Oracle Cloud Infrastructure Object Storage- Your
function needs to read a JSON file object from an Object Storage bucket named “inputbucket” in compartment “QA-compartment”. Your corporate security standards mandate the use of Resource Principals for this use case. Which two
statements are needed to implement this use case?
A. Set up a policy with the following statement to grant read access to the bucket:allow dynamic-group read-file-dg to
read objects in compartment qa-compartment where target .bucket .name=\\’ input-bucket *
B. Set up the following dynamic group for your function\\’s OCID: Name: read-file-dg Rule: resource.id =
`ocid1.fnfunc.oc1.phx.aaaaaaaakeaobctakezjz5i4ujj7g25q7sx5mvr55pms6f4da\\’
C. Set up a policy to grant all functions read access to the bucket:allow all functions in compartment qacompartment to
read objects in target.bucket.name=\\’input-bucket\\’
D. Set up a policy to grant your user account read access to the bucket:allow user XYZ to read objects in compartment
qa-compartment where target .bucket, name-\\’input-bucket\\’
E. No policies are needed. By default, every function has read access to Object Storage buckets in the tenancy
Correct Answer: AB
When a function you\\’ve deployed to Oracle Functions is running, it can access other Oracle Cloud Infrastructure
resources. For example:
–
You might want a function to get a list of VCNs from the Networking service.
–
You might want a function to read data from an Object Storage bucket, perform some operation on the
data, and then write the modified data back to the Object Storage bucket. To enable a function to access another Oracle
Cloud Infrastructure resource, you have to include the function in a dynamic group, and then create a policy to grant the
dynamic group access to that resource. https://docs.cloud.oracle.com/enus/iaas/Content/Functions/Tasks/functionsaccessingociresources.htm
QUESTION 10
Your organization uses a federated identity provider to login to your Oracle Cloud Infrastructure (OCI)
environment. As a developer, you are writing a script to automate some operation and want to use OCI CLI
to do that. Your security team doesn\\’t allow storing private keys on local machines.
How can you authenticate with OCI CLI?
A. Run oci setup keys and provide your credentials
B. Run oci session refresh –profile
C. Run oci session authenticate and provide your credentials
D. Run oci setup oci-cli-rc –file path/to/target/file
Correct Answer: C
Token-based authentication for the CLI allows customers to authenticate their session interactively, then
use the CLI for a single session without an API signing key. This enables customers using an identity
provider that is not SCIM- supported to use a federated user account with the CLI and SDKs.
Starting a Token-based CLI Session
To use token-based authentication for the CLI on a computer with a web browser:
In the CLI, run the following command. This will launch a web browser.
oci session authenticate
In the browser, enter your user credentials. This authentication information is saved to the .config file.
QUESTION 11
Which two handle Oracle Functions authentication automatically?
A. Oracle Cloud Infrastructure SDK
B. cURL
C. Oracle Cloud Infrastructure CLl
D. Signed HTTP Request
E. Fn Project CLI
Correct Answer: CE
Fn Project CLI you can create an Fn Project CLI Context to Connect to Oracle Cloud Infrastructure and specify —
provider oracle This option enables Oracle Functions to perform authentication and authorization using Oracle Cloud
Infrastructure request signing, private keys, user groups, and policies that grant permissions to those user groups.
QUESTION 12
Your Oracle Cloud Infrastructure Container Engine for Kubernetes (OKE) administrator has created an
OKE cluster with one node pool in a public subnet. You have been asked to provide a log file from one of
the nodes for troubleshooting purpose.
Which step should you take to obtain the log file?
A. ssh into the node using public key.
B. ssh into the nodes using private key.
C. It is impossible since OKE is a managed Kubernetes service.
D. Use the username open and password to login.
Correct Answer: B
Kubernetes cluster is a group of nodes. The nodes are the machines running applications. Each node can be a physical
machine or a virtual machine. The node\\’s capacity (its number of CPUs and amount of memory) is defined when the
node is created. A cluster comprises: – one or more master nodes (for high availability, typically there will be a number
of master nodes) – one or more worker nodes (sometimes known as minions) Connecting to Worker Nodes Using SSH
If you provided a public SSH key when creating the node pool in a cluster, the public key is installed on all worker nodes
in the cluster. On UNIX and UNIX-like platforms (including Solaris and Linux), you can then connect through SSH to the
worker nodes using the ssh utility (an SSH client) to perform administrative tasks. Note the following instructions
assume the UNIX machine you use to connect to the worker node: Has the ssh utility installed. Has access to the SSH
private key file paired with the SSH public key that was specified when the cluster was created. How to connect to
worker nodes using SSH depends on whether you specified public or private subnets for the worker nodes when
defining the node pools in the cluster. Connecting to Worker Nodes in Public Subnets Using SSH Before you can
connect to a worker node in a public subnet using SSH, you must define an ingress rule in the subnet\\’s security list to
allow SSH access. The ingress rule must allow access to port 22 on worker nodes from source 0.0.0.0/0 and any source
port To connect to a worker node in a public subnet through SSH from a UNIX machine using the ssh utility: 1- Find out
the IP address of the worker node to which you want to connect. You can do this in a number of ways: Using kubectl. If
you haven\\’t already done so, follow the steps to set up the cluster\\’s kubeconfig configuration file and (if necessary)
set the KUBECONFIG environment variable to point to the file. Note that you must set up your own kubeconfig file. You
cannot access a cluster using a kubeconfig file that a different user set up. See Setting Up Cluster Access. Then in a
terminal window, enter kubectl get nodes to see the public IP addresses of worker nodes in node pools in the cluster.
Using the Console. In the Console, display the Cluster List page and then select the cluster to which the worker node
belongs. On the Node Pools tab, click the name of the node pool to which the worker node belongs. On the Nodes tab,
you see the public IP address of every worker node in the node pool. Using the REST API. Use the ListNodePools
operation to see the public IP addresses of worker nodes in a node pool. 2- In the terminal window, enter ssh opc@ to
connect to the worker node, where is the IP address of the worker node that you made a note of earlier. For example,
you might enter ssh [email protected]. Note that if the SSH private key is not stored in the file or in the path that the ssh
utility expects (for example, the ssh utility might expect the private key to be stored in ~/.ssh/id_rsa), you must explicitly
specify the private key filename and location in one of two ways: Use the -i option to specify the filename and location of
the private key. For example, ssh -i ~/.ssh/ my_keys/my_host_key_filename [email protected] Add the private key
filename and location to an SSH
configuration file, either the client configuration file (~/.ssh/config) if it exists, or the system-wide client
configuration file (/etc/ssh/ssh_config). For example, you might add the following:
Host 192.0.2.254 IdentityFile ~/.ssh/my_keys/my_host_key_filename
For more about the ssh utility\\’s configuration file, enter man ssh_config Note also that permissions on the
private key file must allow you read/write/execute access, but prevent other users from accessing the file.
For example, to set appropriate permissions, you might enter chmod 600 ~/.ssh/my_keys/
my_host_key_filename. If permissions are not set correctly and the private key file is accessible to other
users, the ssh utility will simply ignore the private key file.
QUESTION 13
You have two microservices, A and B running in production. Service A relies on APIs from service B. You want to test
changes to service A without deploying all of its dependencies, which includes service B.
Which approach should you take to test service A?
A. Test against production APIs.
B. Test using API mocks.
C. There is no need to explicitly test APIs.
D. Test the APIs in private environments.
Correct Answer: B
Testing using API mocks Developers are frequently tasked with writing code that integrates with other system
components via APIs. Unfortunately, it might not always be desirable or even possible to actually access those systems
during development. There could be security, performance or maintenance issues that make them unavailable ? or they
might simply not have been developed yet. This is where mocking comes in: instead of developing code with actual
external dependencies in place, a mock of those dependencies is created and used instead. Depending on your
development needs this mock is made “intelligent” enough to allow you to make the calls you need and get similar
results back as you would from the actual component, thus enabling development to move forward without being
hindered by eventual unavailability of external systems you depend on
leads4pass Oracle Discount Code 2021
The latest Oracle exam discount code for 2021. leads4pass is valid throughout the year.
Select the purchased test questions and enter the discount code in the “Promotion Code:” input box to enjoy a 15% discount!
For the full Oracle 1z0-1084-20 exam dumps from leads4pass 1z0-1084-20 Dumps pdf or Dumps VCE visit: https://www.leads4pass.com/1z0-1084-20.html (Q&As: 72 dumps)
ps.
Get free Oracle 1z0-1084-20 dumps PDF online: https://drive.google.com/file/d/1UuRcSyNEGxBxPK9IMlErLQ4tkPCvxWIt/
Comments on '[2021.5] Get the latest Oracle 1z0-1084-20 exam practice questions and free Pdf dumps from Leads4Pass' (0)
Comments Feed
Comments are closed.