Full Version Latest Cisco 350-018 Dumps Exam Questions And Youtube Free Demo
The best and most updated Cisco CCIE 350-018 dumps exam training materials, latest Cisco CCIE 350-018 exam training material in PDF format, which is a very common format found in all computers and gadgets.
【Full Version】All the Cisco 350-018 dumps exam practice questions and answers are revised by the skillful experts. Download the Cisco 350-018 dumps exam pdf readers that are available for free.
Question No : 1
Which two statements about Network Edge Authentication Technology (NEAT) are true? (Choose two.)
A. It can be configured on both access ports and trunk ports.
B. It allows you to configure redundant links between authenticator and supplicant switches
C. It can be configured on both access ports and EtherChannel ports.
D. It supports port-based authentication on the authenticator switch.
E. It conflicts with auto-configuration
F. It requires a standard ACL on the switch port.
Answer: A,D
Question No : 2
During the establishment of an Easy VPN tunnel, when is XAUTH performed?
A. at the end of IKEv1 Phase 2
B. at the beginning of IKEv1 Phase 1
C. at the end of Phase 1 and before Phase 2 starts in IKEv1 and IKEv2
D. at the end of Phase 1 and before Phase 2 starts in IKEv1
Answer: D
Question No : 3
Refer to the exhibit.
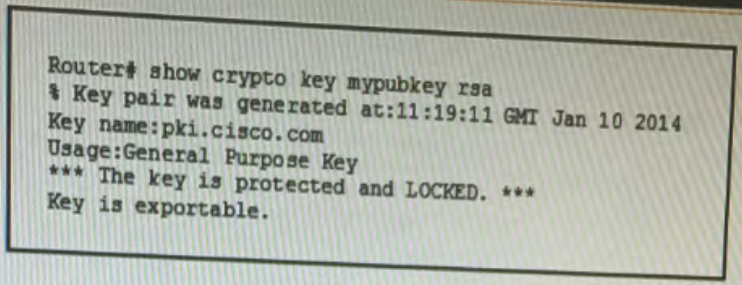
You executed the show crypto key mypubkey rsa command to verify that the RSA key is protected and it generated the given output. What command must you have entered to protect the key? 350-018 dumps
A. crypto key decrypt rsa name pki.cisco.com passphrase CiscoPKI
B. crypto key zeroize rsa CiscoPKI
C. crypto key export rsa pki.cisco.com pem url flash: 3des CiscoPKI
D. crypto key lock rsa name pki.cisco.com passphrase CiscoPKI
E. crypto key import rsa pki.cisco.com pem url nvram: CiscoPKI
Answer: D
Question No : 4
In Cisco Wireless LAN Controller (WLC) , which web policy enables failed Layer 2 authentication to fall back to WebAuth authentication with a user name and password ?
A. Splash Page Web Redirect
B. B. Passthough
C. C.On MAC Filter Failure
D. D. Authentcaiton
E. E.Conditional Web Redirect
Answer: C
Question No : 5
Which three IP resources is IANA responsible for? (Choose three.)
A. IP address allocation
B. detection of spoofed address
C. criminal prosecution of hackers
D. autonomous system number allocation
E. root zone management in DNS
F. BGP protocol vulnerabilities
Answer: A,D,E
Question No : 6
Which two options correctly describe Remote Triggered Black Hole Filtering (RFC 5635)? (Choose two.)
A. RTBH destination based filtering can drop traffic destined to a host based on triggered entries in the FIB.
B. RTBH source based filtering will drop traffic from a source destined to a host based on triggered entries in the RIB
C. Loose uRPF must be used in conjunction with RTBH destination based filtering
D. Strict uRPF must be used in conjunction with RTBH source based filtering
E. RTBH uses a discard route on the edge devices of the network and a route server to send triggered route updates
F. When setting the BGP community attribute in a route-map for RTBH use the no-export community unless BGP confederations are used then use local-as to advertise to sub-as confederations
Answer: A,E
Question No : 7
Which command sets the key-length for the IPv6 SeND protocol? 350-018 dumps
A. ipv6 nd inspection
B. ipv6 nd ra-interval
C. ipv6 nd prefix
D. ipv6 nd secured
E. ipv6 nd ns-interval
Answer: D
Question No : 8
What is the purpose of aaa server radius dynamic-author command?
A. Enables the device to dynamically receive updates from a policy server
B. Enables the switch to automatically authorize the connecting device if all the configured RADIUS servers are unavailable
C. Impairs the ability to configure RADIUS local AAA
D. This command disables dynamic authorization local server configuration mode.
Answer: A
Question No : 9
What Context-Based Access Control (CBAC) command sets the maximum time that a muter running Cisco IOS will wait for a new TCP session to reach the established state?
A. ip inspect max-incomplete
B. ip inspect tcp idle-time
C. ip inspect tcp finwait-time
D. ip inspect udp idle-time
E. ip inspect tcp synwait-time
Answer: E
Question No : 10
What does the Common Criteria (CC) standard define?
A. The current list of Common Vulnerabilities and Exposures (CVEs)
B. The U.S standards for encryption export regulations
C. Tools to support the development of pivotal, forward-looking information system technologies
D. The international standards for evaluating trust in information systems and products
E. The international standards for privacy laws
F. The standards for establishing a security incident response system
Answer: D
2017 hottest Cisco 350-018 dumps exam study guide and practice materials are written according to the latest 350-018 real IT exams. 100% success and guarantee to pass 350-018 exam test quickly and easily at the first time.
Related: http://www.braindump4it.com/latest-microsoft-mb6-700-exam/
Comments on 'Full Version Latest Cisco 350-018 Dumps Exam Questions And Youtube Free Demo' (0)
Comments Feed
Comments are closed.